By Kalle Bjorn, Director – Systems Engineering, Fortinet
Over the past few days, FortiGuard Labs has been observing a surge in an email spam campaign delivering the latest GandCrab v2.1 ransomware. This article provides a basic overview of this malicious campaign and points out details that can help users identify it.
Spam campaign
The image below is a screenshot from our KTIS (Kadena Threat Intelligence System) that shows the overview of a single spam campaign that led to a GandCrab v2.1 sample being delivered as a payload.
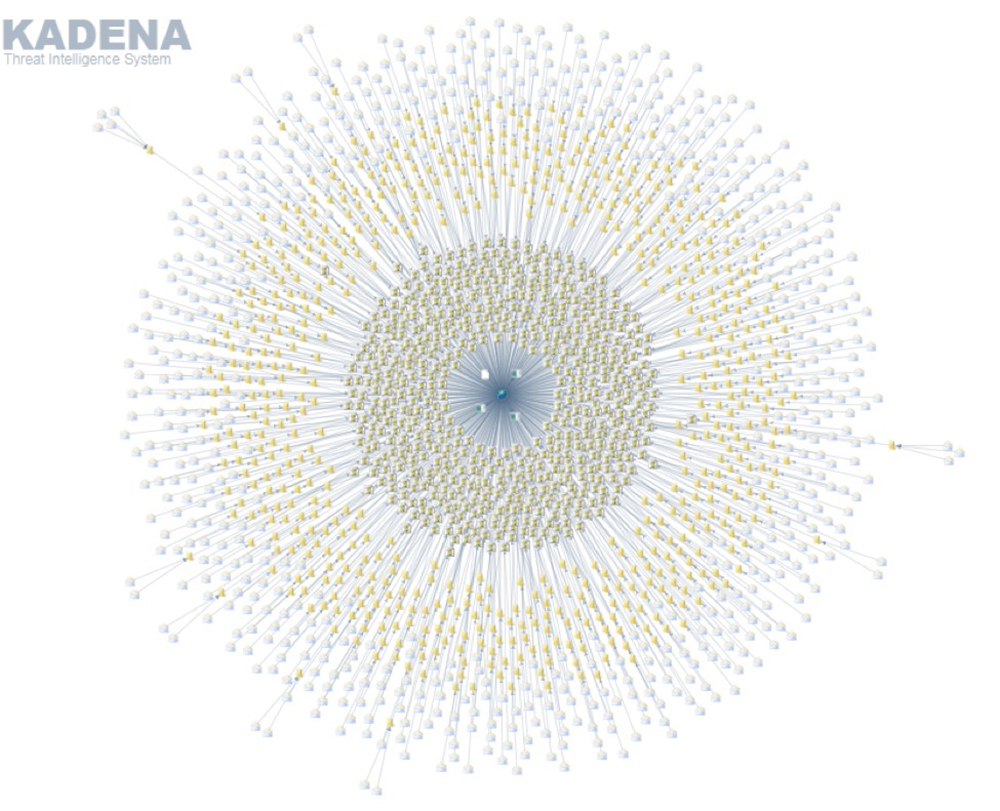
Isolating a branch from the illustration allows us to look at the campaign in more detail, as shown in the following image.
This figure reveals that multiple emails include a Javascript attachment, which when executed downloads a Gandcrab v2.1 variant from a malicious URL.
The graph also shows that at the time of this writing, three unique (different) hashes of Gandcrab v2.1 had already been hosted from the URL.
This means that newly created samples are being pushed simultaneously, possibly with different configurations, or simply to evade specific file signatures. Not limiting itself to Gandcrab, the entity behind this IP address is also hosting other malware such as Phorpiex, which is a worm that allows backdoor access and control, and IRCbot which is a Trojan that can provide attackers with remote access to infected system, as well as a coin miner.

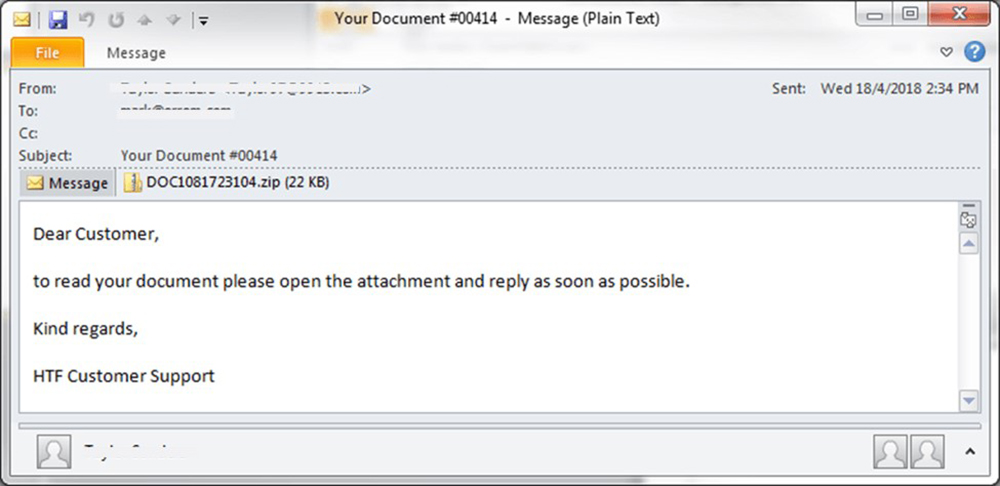
As mentioned previously, the email spam samples include attached JavaScripts hidden inside archives with the filename format DOC<NUMBERS>.zip.
Their contents are all practically the same as those shown in the next figure. Samples observed contained the following subjects:
- Document #<NUMBERS>
- Invoice #<NUMBERS>
- Order #<NUMBERS>
- Payment #<NUMBERS>
- Payment Invoice #<NUMBERS>
- Ticket #<NUMBERS>
- Your Document #<NUMBERS>
- Your Order #<NUMBERS>
- Your Ticket #<NUMBERS>
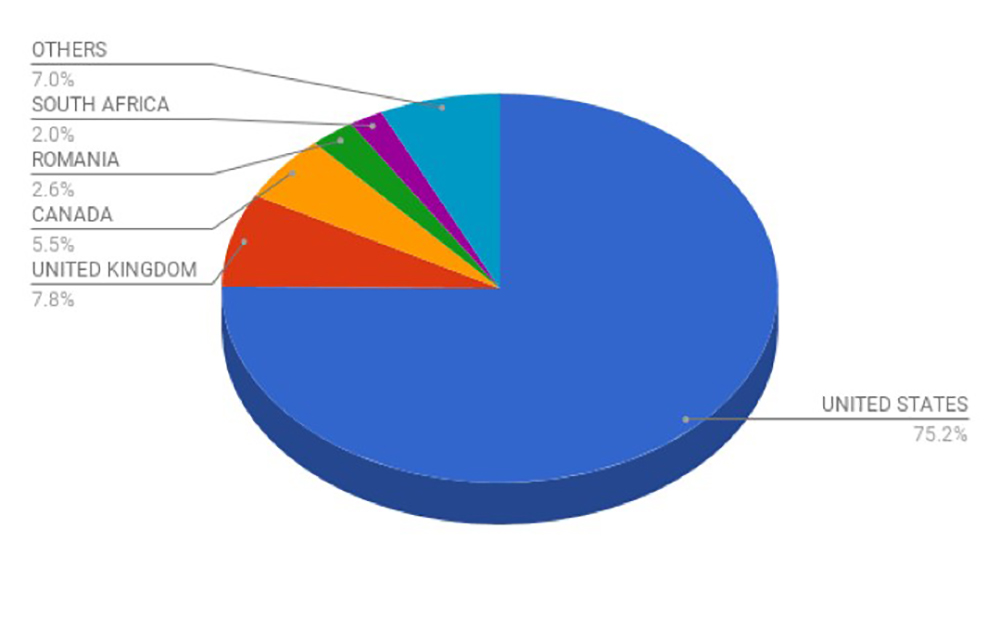
Geographical distribution
The graph below details the spam distribution in terms of the email recipient domains gathered from the collected spam emails over the past week. As can be seen, mail servers hosted in the US are currently the primary recipients of this campaign.
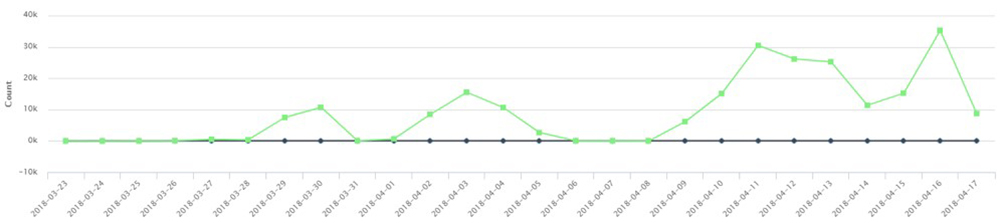
On the other hand, the next graph below shows a more general perspective of GandCrab’s actual infection during the past month. Based on timing alone, it can be observed that infection had already gone up at the time of this campaign’s discovery.
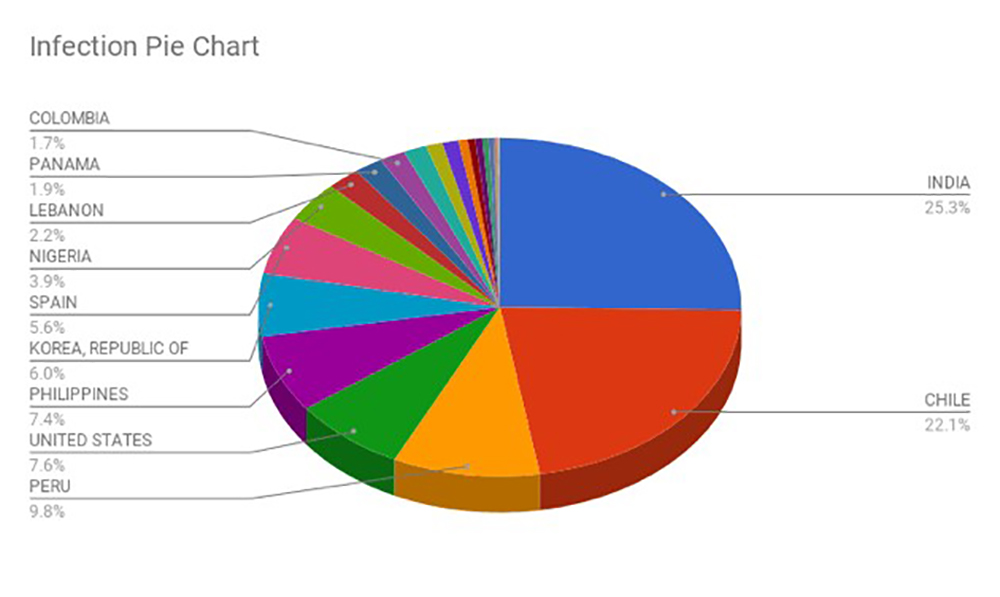
With regards to actual successful GandCrab infections, India is in the top spot, as shown in the following graph.
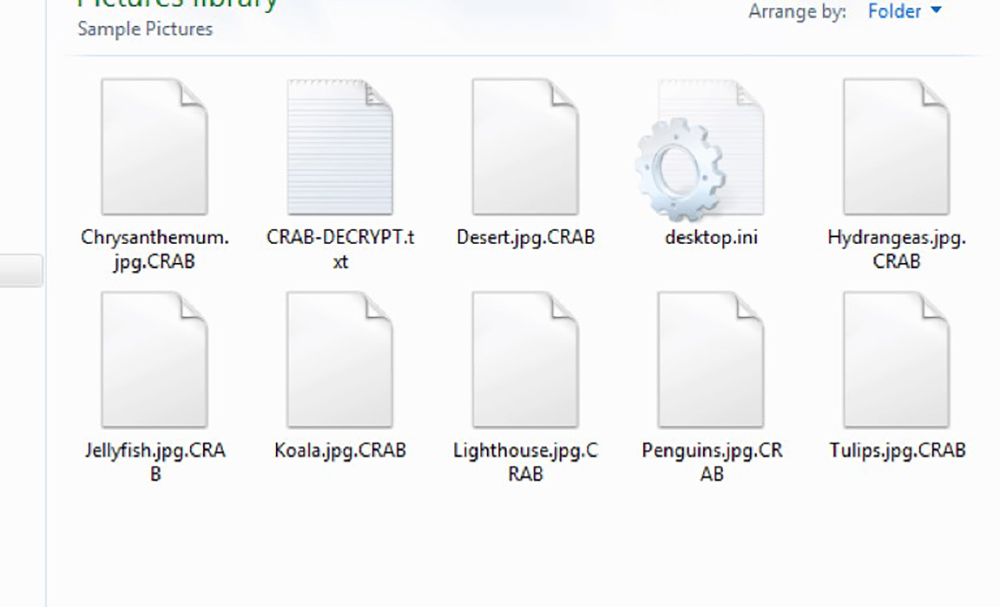
File recovery
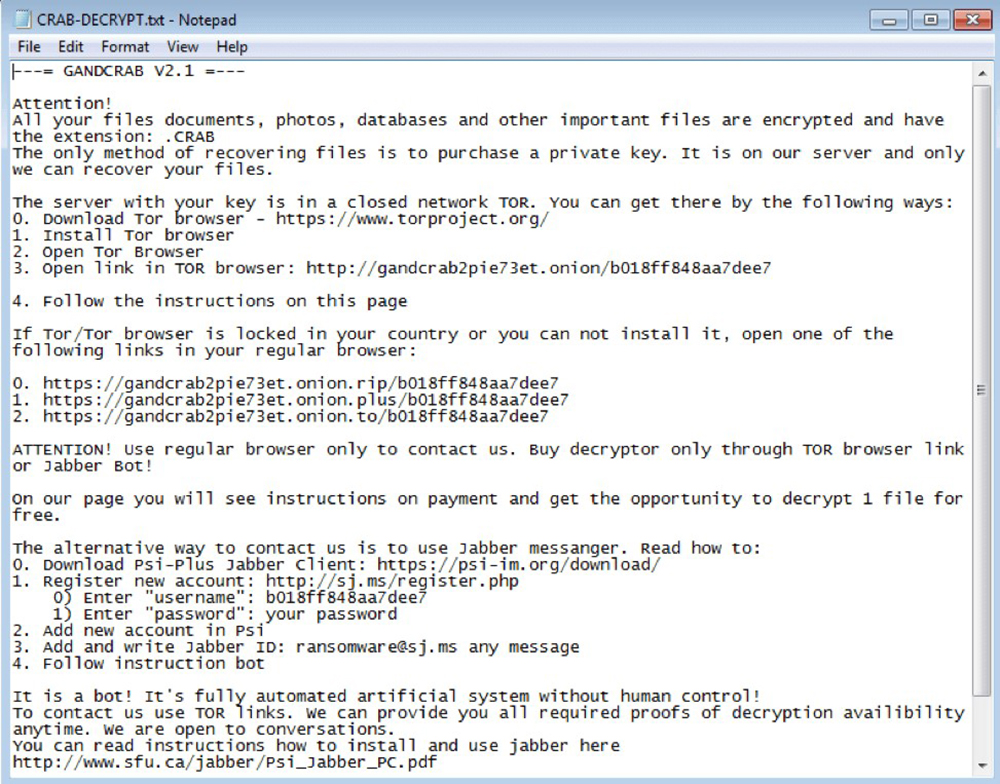
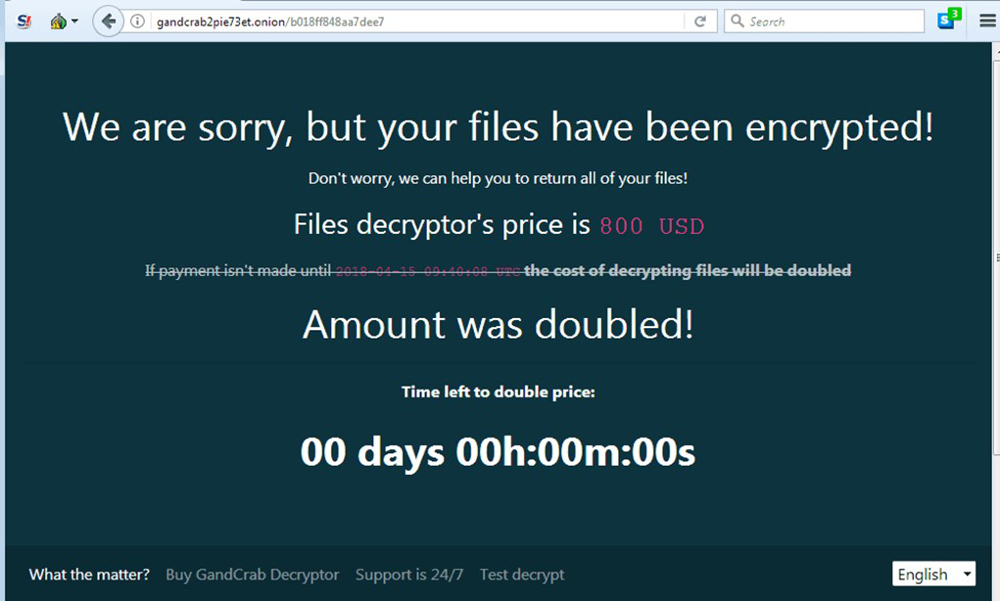
The ransom note contains a link to an onion site that the user has to visit using a TOR browser – which is a browser designed for anonymous internet browsing and downloading – in order to purchase a file decryptor.
The page displays the usual ransomware information, such as further instructions and the initial ransom amount, which will be doubled after a certain time. However, we discourage users from paying the ransom as this does not guarantee any actions from the threat actors.
Conclusion
GandCrab ransomware, or any type of ransomware for that matter, can cause irreversible damage to an infected system.
The best defence against these kinds of attacks is good cyber hygiene and safe practices. In this case, remember that it is always important to be cautious about unsolicited emails, especially those with executable attachments.
In addition, if all else fails, make sure you always have a backup stored in an isolated network environment in order to successfully recover a compromised system.
As always, FortiGuard Labs will continue monitoring GandCrab’s activity, as well as other malware being distributed by these spam campaigns.
Click below to share this article






