Nick Lowe, Regional Director, Northern Europe at Check Point shows why conventional enterprise security defences cannot cope with the latest generation of cyber-attacks, and how those defences must evolve
Over the past 30 years, both cyberattacks and security protections have rapidly evolved. Looking back, it’s easy to identify successive generations of attacks and security solutions. It’s also possible to see the point at which the pace of attack evolution started to exceed the levels of security that most businesses have deployed. Attacks targeting enterprises today are the most advanced and destructive ever seen – yet the security deployed by most businesses is generationally outdated and incapable of protecting against them.
What happened?
There are several reasons why attacks are outpacing the security necessary to prevent them. The most obvious is that attackers have absolutely zero constraints in developing new and advanced techniques. In contrast, businesses have change control procedures, budgetary, compliance and other operational constraints – which all restrain security advances.
Another restriction is the traditional check-box method of building security infrastructures, in which a specific security technology is deployed to defend against a specific type of attack or to protect a specific service. This point solution approach was effective in dealing with earlier generations of attacks. However, today’s attacks are multi-dimensional, multi-stage, multi-vector and polymorphic, with the ability to exploit the gaps left by piecemeal security deployments.
The stark reality is that despite their best efforts, most business security defences are generationally behind the level of attacks they are facing and we must close that security generation gap. Properly protecting a business’s IT operations today requires a new, holistic approach to security: an integrated, unified infrastructure that prevents attacks in real time.
First, let’s examine how the generations of cyberattacks – and the corresponding security defences – have evolved.
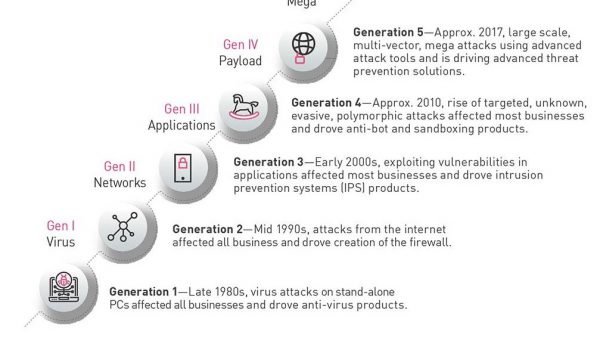
Generations of attacks and security
As networking developed through the 1970s and 80s, leading to the growth of the Internet in the 90s, it’s possible to clearly see the generational advances in attacks and the corresponding protections, with each generation becoming more sophisticated than its predecessor.
The mass availability and use of PCs in the 1980s signalled the start of Gen I attacks, with viruses that could replicate themselves, such as 1986’s Brain virus. These viruses moved at walking speed, spread from one PC to another by floppy disk and drove the development of commercial anti-virus software.
Gen II attacks emerged in the 1990s with networking and the Internet. This opened the gates for malicious software and intrusion attempts like the 1994 theft of over US$ 10million from Citibank, leading to the development of the network firewall. The combination of firewall and anti-virus products became essential to protect businesses, and these products formed the foundation of enterprise security infrastructures. They also started the ‘point solution’ security model of selecting and deploying different products to protect against threats.
Gen III attacks emerged in the early 2000s as attackers learned to exploit vulnerabilities in all components of IT infrastructure. Examples include the SQLSlammer worm, which attacked vulnerabilities in Microsoft SQL Server and became the fastest spreading worm ever. This era also saw an explosion of security technologies and products. As a result, the point solution security model became over-complex and hard to manage. Importantly, the protection delivered by enterprise security began to fall behind the speed and sophistication of attacks.
Gen IV emerged around 2010 as attackers reached new levels of sophistication and their methods became professional. These attacks made headlines in mainstream media because of their public impact – such as the massive breach at US retailer Target which compromised the private information of up to 110 million consumers. This generation also clearly marked the point where detection-based security was no longer enough – organisations now needed to defend against zero-day attacks with techniques such as sandboxing. Security infrastructures became more complex than ever before.
The security generation gap
This brings us to today’s Gen V attacks, which move with unprecedented speed across networks, cloud and mobile devices, and easily overwhelm earlier generations of non-integrated, detect-only technologies. So just how effective are today’s enterprise security infrastructures against these successive generations of attacks?
To establish the extent of the generation gap between threats and security, we recently surveyed nearly 450 security professionals worldwide about their security infrastructures. The results show that enterprise security lags dangerously behind the level of attacks it must protect against – most businesses are only at Gen II or Gen III of security.
With early generations of attacks, it was effective to simply add a new security product for every new type of attack. However, this point-solution approach no longer works. Enterprises end up with a security estate comprising 15-to-20 security products working in detect-only mode: these cannot prevent attacks and they also absorb a huge amount of management time.
The result is that typical point solution IT security infrastructures cannot protect against the current generation of attacks, as highlighted by a key survey finding that 31% of our sample using consolidated security architectures identify and remediate attacks 20x faster and at 1% of the cost compared with those using point, best-of-breed security products.
Gen V security is needed
Businesses must build a plan to move from their Gen II or Gen III point solution security deployment to a Gen V security infrastructure. Gen V security is advanced threat prevention that uniformly prevents attacks on a business’ entire IT infrastructure with single-console central management for administration, monitoring and response. This not only protects against Gen V attacks but also is built using an infrastructure where businesses are able to easily add security capabilities as threats and IT environments evolve.
This consolidated cybersecurity architecture provides real-time threat prevention against known and unknown threats, leveraging advanced threat prevention and zero-day technologies. It uses automatic threat intelligence sharing across all networks, endpoints, cloud and mobile to seal gaps across the entire enterprise network.
The evolution of cyberattacks and cybersecurity over the past 30 years has been rapid, and is still accelerating. Today, the security deployed by businesses is at a concerning inflection point because most IT security infrastructures are only at the Gen II or Gen III level of security, which cannot cope with advanced Gen V attacks.
To resolve this problem, we must counter Gen V attacks with Gen V security: advanced threat prevention that uniformly prevents attacks on a business entire IT infrastructure. This approach will firmly close the security generation gap – and ensure it stays closed.
Click below to share this article