A survey from Ericom Software reveals four out of five organizations plan to begin their Zero Trust security solution rollout within 12 months but key challenges complicate adoption.
Ericom Software, a leader in cloud cybersecurity solutions for secure web and application access and developer of the ZTEdge Cloud Security Platform, has announced publication of the results of its inaugural Zero Trust Market Dynamics Survey.
This was conducted by Dr Chase Cunningham, Ericom’s Chief Strategy Officer and former Forrester Analyst focused on Zero Trust security.
The survey was designed to assess the market’s perception of the Zero Trust security framework, explore organizations’ plans for adoption and implementation and identify key issues that are inhibiting their moves to Zero Trust.
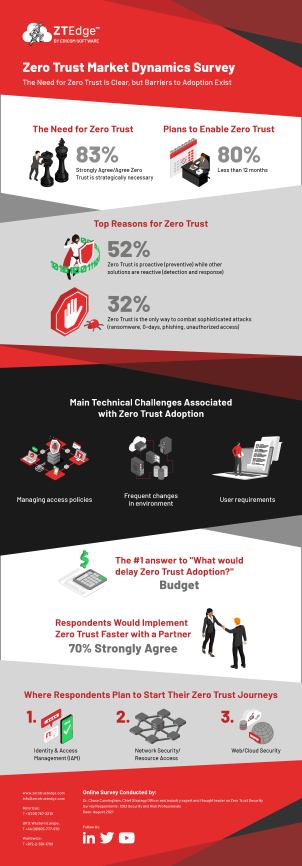
Over a decade after the Zero Trust security concept was first introduced, survey results indicate that Zero Trust solutions are being widely adopted. Spurred by the recent sharp increase in ransomware and other sophisticated cyberattacks, the majority of organizations – 80% – have concrete plans to enable Zero Trust security solutions within the next year, with over half planning to begin implementation during 2021.
Of the almost 1,300 security and risk professionals who participated in the July 2021 survey, 83% indicated that they consider Zero Trust to be an essential strategy for their organizations, according to Dr Cunningham.
Almost all respondents believe that adopting a Zero Trust cybersecurity approach was essential in preventing or limiting the success of cyberattacks. As far as where they plan to start their Zero Trust security programs, the most popular area of initial focus was Identity and Access Management, followed by Network Security and Web Security.
While respondents were bullish on the necessity of adopting a Zero Trust security approach, they are less confident in their abilities to successfully implement solutions. Over 70% feel that having a partner to help implement Zero Trust would speed the process, while budget restrictions and prioritization of other strategic security initiatives are most likely to delay Zero Trust programs from the business perspective.
On the IT side of the ledger, respondents identified legacy technology and complexity associated with defining and implementing Zero Trust security policies as significant barriers to successful implementation.
“I was pleased to see the survey results reported significant market momentum around the Zero Trust security framework and am excited about its ability to make a real difference in the security posture of the organizations that adopt it,” said Dr Cunningham. “Security vendors that can help organizations address their pain points around budget, complexity and flexibility will be in a strong position to partner with businesses as they implement their Zero Trust programs.”
Ericom plans to execute the Zero Trust Market Dynamics Survey each year in order to assess changes and trends in the market over time.
We asked Dr Chase Cunningham, Ericom’s Chief Strategy Officer, further questions to find out more.
What are the key issues that are inhibiting moves to Zero Trust security frameworks?
The data in the study highlights a few things that are inhibiting Zero Trust projects. Budget is a concern for many, and the complexity associated with moving off of legacy technologies is called out as well.
It is not surprising that a majority of respondents believe an outside partner, like an MSSP, would accelerate their moves to Zero Trust. Interestingly, the marketing hype associated with Zero Trust – where ‘everything’ is positioned as ZT can also muddy the waters and turn people off.
The good news is that I never have conversations with practitioners that don’t see the value in moving to ZT and it appears the business leadership community is coming onboard as well.
Why do some organizations consider Zero Trust as an essential part of their security strategy?
I think that is because security leadership has gravitated to the concept that if they continue to do the same thing that everyone else has that already failed, they will as well. They see the value in a new more focused approach and can sell that strategy internally.
How can a Zero Trust security framework make a real difference in the security posture of the organizations that adopt it?
The value of a framework in any context, especially in a space as diverse as cybersecurity, is that it helps you understand ‘what goes where’. That’s why I created the Zero Trust eXtended (ZTX) Ecosystem framework years ago, to help leaders translate technology into specific use cases and that helped Zero Trust take off.
Why has Identity and Access Management proven to be so popular?
Everything in IT revolves around access and privileges. No firewall has ever hacked itself, as far as I know. A user or administrator had to have an account to change settings on that device for things to go wrong. So, if you fix or work to fix Identity and Access Management you are addressing a key area of exploitation and you gain a lot of ground quickly.
What developments do you expect to see in the Identity and Access Management market in the next few years?
The use of self-sovereign identity and biometrics will be further integrated into the Identity and Access Management lifecycle and technology space and those organizations and users that adopt these solutions will be able to have fully verified and secured access management across any infrastructure.
Why were some respondents of the survey unconfident in their abilities to successfully implement Zero Trust solutions?
Many organizations are already further along in their Zero Trust journey than they realize, especially those who are in heavily compliant verticals. They have been working towards Zero Trust for a long time without even realizing it, so they have a lead on the market. And that can be tied to organizations that are adopting integrated useable Zero Trust solutions that are broadly applicable which also helps expedite the move to Zero Trust.
Click below to share this article






