Ransomware and cyberattacks are taking place more and more frequently.
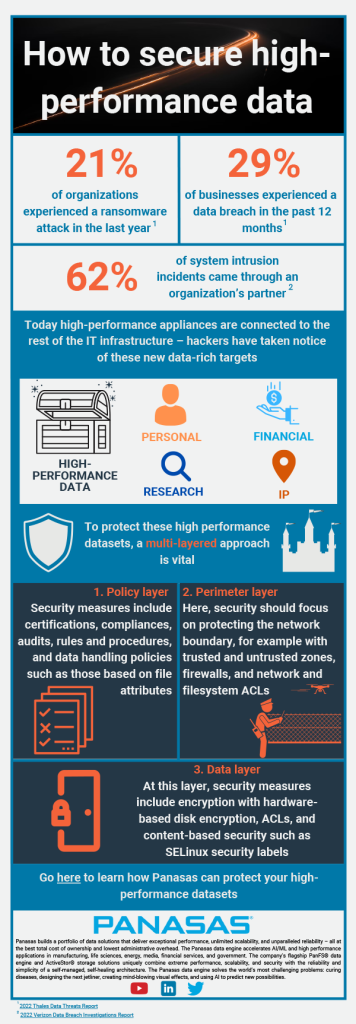
High-performance environments are rich in high-value data, often containing personal, business, financial, IP, or even nationally significant data, meaning that they are at increased risk and must be protected. Yet, traditionally, data protection has not been top of mind for High-Performance Computing (HPC) users.
Historically, as long as their systems were separated from the corporate LAN and the Internet, HPC users didn’t worry about security. This meant that they could avoid the accompanying overhead of security solutions and drive as much performance into their HPC installations as possible.
However, this is no longer the case due to two key trends: first, with the expansion of HPC use cases into manufacturing, Big Data analytics, AI and ML, organisations need to integrate their high-performance appliances into the rest of their infrastructures. Second, hackers are looking for more data-rich targets. Government labs, manufacturers and other high-performance environments are prime targets.
So how can end-users fully protect their high-performance datasets? A multi-layer or ‘defence in depth’ approach, built with trusted partners, is needed.
This should include a policy layer, for example mandatory access controls that confine user programmes and system services to the minimum level of file and data access that they require, a perimeter layer, such as filesystem and network ACLs to manage access permissions across the filesystem or network and the data layer. At the data layer, modern self-encrypting drives, which include hardware-based encryption algorithms built into the drives, are designed in a way that does not impact performance.
The Key Management Interoperability Protocol (KMIP) enables customers to centralise and simplify encryption key management including key generation, escrow and recovery. IT teams should look for fully proven and validated high-performance solutions from expert partners that can be tested.
Click below to share this article


